---->>>>
We are here to proudly present that we have successfully launched a website . here after all blogs and articles will be updated there. Also we here by add old articles to the site.
Catch us at www.hiswat.info
Sunday, October 11, 2009
Thursday, July 30, 2009
Virtual Windows For all
---->>>>
Do you know about online virtual operating system? most probably many company’s provide virtual operating system to their clients for money. Windows4all a website which provides virtual Windows operating system for free.
Windows4all is a Microsoft Silverlight based online virtual operating system, it simulates an operating system inside a web browser. Windows4all.com replicates the desktop environment of a modern operating system. The user can launch applications right away without installation.

Windows4all is web-based and requires Silverlight 2 to operate. currently it includes desktop, taskbar, start menu and sidebar with applications like
* File Explorer
* Internet Explorer
* Video Player
* Rich text editor
* RSS reader
* Notepad
* Paint
* Calculator
* Games like Chess, Solitaire, Spider, Tic-tac-toe
The system also supports installing program functionality. But this program should be developed in Silverlight and have valid URLs for the xap file.
visit Windows4all.Com
Do you know about online virtual operating system? most probably many company’s provide virtual operating system to their clients for money. Windows4all a website which provides virtual Windows operating system for free.
Windows4all is a Microsoft Silverlight based online virtual operating system, it simulates an operating system inside a web browser. Windows4all.com replicates the desktop environment of a modern operating system. The user can launch applications right away without installation.

Windows4all is web-based and requires Silverlight 2 to operate. currently it includes desktop, taskbar, start menu and sidebar with applications like
* File Explorer
* Internet Explorer
* Video Player
* Rich text editor
* RSS reader
* Notepad
* Paint
* Calculator
* Games like Chess, Solitaire, Spider, Tic-tac-toe
The system also supports installing program functionality. But this program should be developed in Silverlight and have valid URLs for the xap file.
visit Windows4all.Com
Free Tutorial Search Engine
---->>>>
Free Tutorial For.Me website which provides you to search tutorials from various sources, Free Tutorial For.Me built via Google search engine.
Free Tutorial For.Me provides search results with easy navigation, it allows users to view PDF documents via scribd.
Free Tutorial For Me

Iif you are searching for any tutorials or PDF documents for particular type just enter the topic name and search it, For instance “Ajax” where you can get list of search results for Ajax topics, where you can easily navigate and view the documents as shown below picture.

Free Tutorial For.Me also allows users to download PDF or any other searched documents by one click on its search result title.
Free Tutorial For.Me website which provides you to search tutorials from various sources, Free Tutorial For.Me built via Google search engine.
Free Tutorial For.Me provides search results with easy navigation, it allows users to view PDF documents via scribd.
Free Tutorial For Me

Iif you are searching for any tutorials or PDF documents for particular type just enter the topic name and search it, For instance “Ajax” where you can get list of search results for Ajax topics, where you can easily navigate and view the documents as shown below picture.

Free Tutorial For.Me also allows users to download PDF or any other searched documents by one click on its search result title.
Monday, June 29, 2009
Microsoft Security Essentials Beta Released
---->>>>
Microsoft unveiled its new free anti virus software Microsoft Security Essentianls Beta for public formerly named “Morro“.
It seems Microsoft Security Essentianls Beta available for limited number of downloads, but you can still download Microsoft Security Essentianls Beta from alternative downloads from softpedia.

Minimum system requirements for Microsoft Security Essentials Beta
* Operating System: Windows XP (Service Pack 2 or Service Pack 3); Windows Vista; Windows 7 (Beta or Release Candidate)
* For Windows XP
CPU with clock speed of 500 MHz or higher
Memory: 256 MB RAM or higher
* For Windows Vista and Windows 7
CPU with clock speed of 1.0 GHz or higher
Memory: 1 GB RAM or higher
* VGA (Display): 800 x 600 or higher
* Storage: 140 MB of available hard-disk space
* An Internet connection is required for installation and to download the latest virus and spyware definitions for Microsoft Microsoft Security Essentials.
* Internet Browser:
Windows Internet Explorer 6.0 or later
Mozilla Firefox 2.0 or later.
Note : Microsoft Security Essentials requires genuine validation, If you are using pirated Windows operating system you cannot install Microsoft Security Essentianls Beta
Download Microsoft Security Essentianls Beta.
Microsoft unveiled its new free anti virus software Microsoft Security Essentianls Beta for public formerly named “Morro“.
It seems Microsoft Security Essentianls Beta available for limited number of downloads, but you can still download Microsoft Security Essentianls Beta from alternative downloads from softpedia.

Minimum system requirements for Microsoft Security Essentials Beta
* Operating System: Windows XP (Service Pack 2 or Service Pack 3); Windows Vista; Windows 7 (Beta or Release Candidate)
* For Windows XP
CPU with clock speed of 500 MHz or higher
Memory: 256 MB RAM or higher
* For Windows Vista and Windows 7
CPU with clock speed of 1.0 GHz or higher
Memory: 1 GB RAM or higher
* VGA (Display): 800 x 600 or higher
* Storage: 140 MB of available hard-disk space
* An Internet connection is required for installation and to download the latest virus and spyware definitions for Microsoft Microsoft Security Essentials.
* Internet Browser:
Windows Internet Explorer 6.0 or later
Mozilla Firefox 2.0 or later.
Note : Microsoft Security Essentials requires genuine validation, If you are using pirated Windows operating system you cannot install Microsoft Security Essentianls Beta
Download Microsoft Security Essentianls Beta.
Windows 7 Pricing and Pre-Order Offer
---->>>>
Microsoft on 25th June announced Windows 7 retail pricing, availability, upgrade and other details. Windows 7 shipping starts on October 22nd & Windows 7 will be available in the following 14 languages English, Spanish, Japanese, German, French, Italian, Dutch, Russian, Polish, Brazilian Portuguese, Korean, Simplified Chinese, Traditional Chinese and Chinese (Hong Kong).
On October 31st, the remaining 21 languages will become available Turkish, Czech, Portuguese, Hungarian, Swedish, Danish, Norwegian, Finnish, Greek, Ukrainian, Romanian, Arabic, Lithuanian, Bulgarian, Estonian, Slovenian, Hebrew, Thai, Croatian, Serbian Latin, and Latvian.
Windows 7 upgrade option program opens today and you can upgrade to windows 7. If you are buying PC from a participating OEM or retailer with Windows Vista Home Premium, Business or Ultimate. You will receive an upgrade to the corresponding version of Windows 7 at little or no cost.
Note : The Windows 7 upgrade option program will be available until January 31st, 2010.
For more details about upgrade offer visit www.windows.com/upgradeoffer
The estimated retail prices for upgrade packaged retail product of Windows 7.
* Windows 7 Home Premium (Upgrade): $119.99
* Windows 7 Professional (Upgrade): $199.99
* Windows 7 Ultimate (Upgrade): $219.99
The estimated retail prices for full packaged retail product of Windows 7.
* Windows 7 Home Premium (Full): $199.99
* Windows 7 Professional (Full): $299.99
* Windows 7 Ultimate (Full): $319.99
Windows 7 Pre-Order Offer
Microsoft today announced pre-order offer for Windows 7 operating system.
The estimated retail prices for Pre-Order offer
* Windows 7 Home Premium Upgrade for $49.**
* Windows 7 Professional Upgrade for $99.**
Note : This offer is available through participating retailers.
For more detailed information regarding, how to grab Windows 7 Pre-Order offer visit : www.microsoft.com/windows/buy/offers/pre-order.aspx
Microsoft on 25th June announced Windows 7 retail pricing, availability, upgrade and other details. Windows 7 shipping starts on October 22nd & Windows 7 will be available in the following 14 languages English, Spanish, Japanese, German, French, Italian, Dutch, Russian, Polish, Brazilian Portuguese, Korean, Simplified Chinese, Traditional Chinese and Chinese (Hong Kong).
On October 31st, the remaining 21 languages will become available Turkish, Czech, Portuguese, Hungarian, Swedish, Danish, Norwegian, Finnish, Greek, Ukrainian, Romanian, Arabic, Lithuanian, Bulgarian, Estonian, Slovenian, Hebrew, Thai, Croatian, Serbian Latin, and Latvian.
Windows 7 upgrade option program opens today and you can upgrade to windows 7. If you are buying PC from a participating OEM or retailer with Windows Vista Home Premium, Business or Ultimate. You will receive an upgrade to the corresponding version of Windows 7 at little or no cost.
Note : The Windows 7 upgrade option program will be available until January 31st, 2010.
For more details about upgrade offer visit www.windows.com/upgradeoffer
The estimated retail prices for upgrade packaged retail product of Windows 7.
* Windows 7 Home Premium (Upgrade): $119.99
* Windows 7 Professional (Upgrade): $199.99
* Windows 7 Ultimate (Upgrade): $219.99
The estimated retail prices for full packaged retail product of Windows 7.
* Windows 7 Home Premium (Full): $199.99
* Windows 7 Professional (Full): $299.99
* Windows 7 Ultimate (Full): $319.99
Windows 7 Pre-Order Offer
Microsoft today announced pre-order offer for Windows 7 operating system.
The estimated retail prices for Pre-Order offer
* Windows 7 Home Premium Upgrade for $49.**
* Windows 7 Professional Upgrade for $99.**
Note : This offer is available through participating retailers.
For more detailed information regarding, how to grab Windows 7 Pre-Order offer visit : www.microsoft.com/windows/buy/offers/pre-order.aspx
Gmail Increased File Attachment to 25 MB
---->>>>
Most of the Email services provides 20 MB of file attachment, Gmail the internet giant also provided 20 MB of attachment. Recently Google Operating System notified the increment in Gmail file attachment.
Gmail help confirms that Gmail file attachment extended to 25 MB. “With Gmail, you can send and receive messages up to 25 megabytes (MB) in size.
Please note that you may not be able to send larger attachments to contacts who use other email services with smaller attachment limits. If your attachment bounces, you should invite them to Gmail”.
You can upload 25 MB of multiple files from your Gmail account, but it’s a little bit tidious job and receiver should use Gmail, otherwise it’s diffcult to receive 25 MB of files.
Most of the Email services provides 20 MB of file attachment, Gmail the internet giant also provided 20 MB of attachment. Recently Google Operating System notified the increment in Gmail file attachment.
Gmail help confirms that Gmail file attachment extended to 25 MB. “With Gmail, you can send and receive messages up to 25 megabytes (MB) in size.
Please note that you may not be able to send larger attachments to contacts who use other email services with smaller attachment limits. If your attachment bounces, you should invite them to Gmail”.
You can upload 25 MB of multiple files from your Gmail account, but it’s a little bit tidious job and receiver should use Gmail, otherwise it’s diffcult to receive 25 MB of files.
Friday, May 1, 2009
Microsoft Office 14 Screenshots Leaked
---->>>>

After Windows 7 Microsoft is working on Microsoft Office 9 Suite. Rumors have Office 14 due in 2010, but Microsoft may choose to time its release to coincide with that of Windows 7 later this year. For now Microsoft is expected to unveil details about the next-generation suite before the second half of this year. Below you can see the Office 14 About page, which sports an attractive little sidebar for opening, saving, or creating new documents
Here are some more Screenshots:-




After Windows 7 Microsoft is working on Microsoft Office 9 Suite. Rumors have Office 14 due in 2010, but Microsoft may choose to time its release to coincide with that of Windows 7 later this year. For now Microsoft is expected to unveil details about the next-generation suite before the second half of this year. Below you can see the Office 14 About page, which sports an attractive little sidebar for opening, saving, or creating new documents
Here are some more Screenshots:-



Saturday, April 25, 2009
Funny Google Image Search with JavaScript
---->>>>
We always use to search images in Google image search, did u ever tried to search images with funny java Script trick. We would like to share here tricks for flying images in Google image search.
This trick is easy to implement, just search for anything in Google image search.
Steps
1. For instance if your searching for flowers in Google image search and to implement JavaScript clear the current URL in address bar (Google Image search result URL )
2. Copy from the NotePad(1KB) and Paste the JavaScript in address bar.
http://www.ziddu.com/download/4458982/Javascript.txt.html
Eg

3. Now you can see the images circling your browser in Google image search result.
Note : This JavaScript works on Google image search results and flickr.
We always use to search images in Google image search, did u ever tried to search images with funny java Script trick. We would like to share here tricks for flying images in Google image search.
This trick is easy to implement, just search for anything in Google image search.
Steps
1. For instance if your searching for flowers in Google image search and to implement JavaScript clear the current URL in address bar (Google Image search result URL )
2. Copy from the NotePad(1KB) and Paste the JavaScript in address bar.
http://www.ziddu.com/download/4458982/Javascript.txt.html
Eg

3. Now you can see the images circling your browser in Google image search result.
Note : This JavaScript works on Google image search results and flickr.
Send Email Anonymously with Send-Email.org
---->>>>If you are going out of your room or house unfortunately you have missed to send a text email and you have logged out from email account. In this case you can use send-email.org
Send-email.org provides free anonymous email service where you can send email from your own email address, without logging into your email account.
Website : www.send-email.org
Note : you should not use this service for any other illegal purpose.
Send-email.org provides free anonymous email service where you can send email from your own email address, without logging into your email account.
Website : www.send-email.org
Note : you should not use this service for any other illegal purpose.
Tuesday, April 21, 2009
Animated Guide to Build Your PC
---->>>>
Most of the time all of them like to assemble their PC by themselves, but the people who dont have knowledge about hardware components in computers a little bit diffcult task to assemble PC.
If you are not good in assembling a PC here is a website called PC it Yourself, which helps you to build your PC step by step and they also provide animated guide via YouTube.

PC it Yourself helps how and where to choose your hardwares and vendors, animated guide to build PC and installing operaing system in a step by step process.
YouTube : www.youtube.com/user/pcityourself.
Website : www.pcityourself.com
Most of the time all of them like to assemble their PC by themselves, but the people who dont have knowledge about hardware components in computers a little bit diffcult task to assemble PC.
If you are not good in assembling a PC here is a website called PC it Yourself, which helps you to build your PC step by step and they also provide animated guide via YouTube.

PC it Yourself helps how and where to choose your hardwares and vendors, animated guide to build PC and installing operaing system in a step by step process.
YouTube : www.youtube.com/user/pcityourself.
Website : www.pcityourself.com
Free Online Converter - CometDocs
---->>>>
There are lot online file converters but we found a website called cometdocs where you can convert almost all type of files into a specified action or event.
Cometdocs not only acts as a file converter it acts as a data converter also it find outs information from the given input file. It’s easy to upload files and select a type what you have to do with cometdocs and enter your email the file will be converted to the selected type and you will be getting file in your email inbox.

Let’s see what are the files and conversions are available in cometdocs.
1. Converts CSV file to a delimited format.
2. File converter for PDF conversion (Adobe Acrobat) to text file.
3. PDF info - extracts and prints the contents of the info of the given file.
4. Legacy file to PDF conversion.
5. Diff online - Compare two files and return the lines where they are different in standard.
6. Mp3 info - Gets the tag information of ID3v1 and ID3v2.
7. XML lint - pretty printer for XML documents
8. Converts HTML file to RSS feed
9. Convert ls directory listing to Google site map XML.
10. Audio converters - Overview of music converters for conversion to and from mp3, wav etc.
11. iTunes XML to M3U converter.
12. Metastock data conversion
13. Legacy word processor to Microsoft Word conversions.
14. Legacy spreadsheet to Microsoft Excel conversions.
15. Determines unknown file format.
16. Unix2Dos - Convert those pesky end of line (^M) characters to normal newlines.
17. Dos2Unix - Convert end of line handling for Unix-based systems.
18. Mac2Unix - Convert text files to the proper line terminator on Unix coming from the mac format.
19. File sort - Sorts the lines or records in your file in ascending ASCII order.
20. Convert toPalm Pilot doc file from text.
21. ‘iconv’ converter.
22. Convert Excel .xls to CSV.
23. ASCII to EBCDIC data conversion.
24. Fixed record format to delimited data conversion.
25. Convert delimited file to a fixed record format.
Visit website : www.cometdocs.com
There are lot online file converters but we found a website called cometdocs where you can convert almost all type of files into a specified action or event.
Cometdocs not only acts as a file converter it acts as a data converter also it find outs information from the given input file. It’s easy to upload files and select a type what you have to do with cometdocs and enter your email the file will be converted to the selected type and you will be getting file in your email inbox.

Let’s see what are the files and conversions are available in cometdocs.
1. Converts CSV file to a delimited format.
2. File converter for PDF conversion (Adobe Acrobat) to text file.
3. PDF info - extracts and prints the contents of the info of the given file.
4. Legacy file to PDF conversion.
5. Diff online - Compare two files and return the lines where they are different in standard.
6. Mp3 info - Gets the tag information of ID3v1 and ID3v2.
7. XML lint - pretty printer for XML documents
8. Converts HTML file to RSS feed
9. Convert ls directory listing to Google site map XML.
10. Audio converters - Overview of music converters for conversion to and from mp3, wav etc.
11. iTunes XML to M3U converter.
12. Metastock data conversion
13. Legacy word processor to Microsoft Word conversions.
14. Legacy spreadsheet to Microsoft Excel conversions.
15. Determines unknown file format.
16. Unix2Dos - Convert those pesky end of line (^M) characters to normal newlines.
17. Dos2Unix - Convert end of line handling for Unix-based systems.
18. Mac2Unix - Convert text files to the proper line terminator on Unix coming from the mac format.
19. File sort - Sorts the lines or records in your file in ascending ASCII order.
20. Convert toPalm Pilot doc file from text.
21. ‘iconv’ converter.
22. Convert Excel .xls to CSV.
23. ASCII to EBCDIC data conversion.
24. Fixed record format to delimited data conversion.
25. Convert delimited file to a fixed record format.
Visit website : www.cometdocs.com
Thursday, April 16, 2009
Bypass Genuine Validation For Downloading Packages
---->>>>
Most of the users use pirated Operating system especially Windows XP, while downloading small packages for the operating system Microsoft asks you to validate and download the package.
In this case its a problem to download packages and you will get a message as shown below.

Now just copy the File name and search in file search engines like Findfiles.com or any other file search engines.

Find Files
Findfiles.com gives you direct link from Microsoft servers and also mirror download.
Now your package is ready to install even if you are using pirated OS.
Most of the users use pirated Operating system especially Windows XP, while downloading small packages for the operating system Microsoft asks you to validate and download the package.
In this case its a problem to download packages and you will get a message as shown below.

Now just copy the File name and search in file search engines like Findfiles.com or any other file search engines.

Find Files
Findfiles.com gives you direct link from Microsoft servers and also mirror download.
Now your package is ready to install even if you are using pirated OS.
Scan Links for Harmful Threats
---->>>>
Find out any website is affected with any threat via onlinelinkscan.com. Where you can find scanned threat information from various resources like AVG, Google, SiteTruth and Phish Tank.

Features
* Easy to find threats for a website URL from various resources like AVG, Google, SiteTruth and Phish Tank.
* Says link status of a URL
* File Size of the website
* Overall result whether the site is secured or not
Visit : onlinelinkscan.com
Find out any website is affected with any threat via onlinelinkscan.com. Where you can find scanned threat information from various resources like AVG, Google, SiteTruth and Phish Tank.

Features
* Easy to find threats for a website URL from various resources like AVG, Google, SiteTruth and Phish Tank.
* Says link status of a URL
* File Size of the website
* Overall result whether the site is secured or not
Visit : onlinelinkscan.com
Check User Name Availability For Multiple Websites
---->>>>
If you are checking to register user name for your brand or company in multiple social network sites, its a tough job to check every site whether user name is available or not.
But you can check easily whether your brand name or your selected name is available in all social network sites using Namechk.Com

If you are checking to register user name for your brand or company in multiple social network sites, its a tough job to check every site whether user name is available or not.
But you can check easily whether your brand name or your selected name is available in all social network sites using Namechk.Com

Mathematical Cheat Sheets
---->>>>
If you are searching for mathematical formulas to solve a problem, we found a website called ecalc where you can get lot of Mathematical cheat sheets.
ecalc provides standard mathematical formulas and cheat sheet books for free.
* Algebra Help Math Sheet
* Geometry Math Sheet
* Trigonometry Definition Math Sheet
* Trigonometry Laws and Identities Math Sheet
* Calculus Derivatives and Limits Math Sheet
* Calculus Integrals Math Sheet
You can view online and download the above mentioned math sheets for free.

Download Math Sheet
If you are searching for mathematical formulas to solve a problem, we found a website called ecalc where you can get lot of Mathematical cheat sheets.
ecalc provides standard mathematical formulas and cheat sheet books for free.
* Algebra Help Math Sheet
* Geometry Math Sheet
* Trigonometry Definition Math Sheet
* Trigonometry Laws and Identities Math Sheet
* Calculus Derivatives and Limits Math Sheet
* Calculus Integrals Math Sheet
You can view online and download the above mentioned math sheets for free.

Download Math Sheet
Saturday, April 11, 2009
Mobile Secret Codes
NOKIA
* Use at Own Risk
1 Imagine ur cell battery is very low, u r expecting an
important call and u don't have a charger.
Nokia instrument comes with a reserve battery. To
activate,key is "*3370#"
Ur cell will restart with this reserve and ur instrument
will show a 50% incerase in battery.
This reserve will get charged when u charge ur cell
next
time.
*3370# Activate Enhanced Full Rate Codec (EFR)-Your phone
uses the best sound quality but talk time is reduced by approx.
5%
#3370# Deactivate Enhanced Full Rate Codec( EFR)
*#4720# Activate Half Rate Codec - Your phone uses a
lower
quality sound
but you should gain approx 30% more Talk Time
*#4720# Deactivate Half Rate Codec
2 *#0000# Displays your phones software version,
1st Line : Software Version,
2nd Line : Software Release Date,
3rd Line : Compression Type
3 *#9999# Phones software v ersion if *#0000# does not work
4 *#06# For checking the International Mobile Equipment
Identity
(IMEI Number)
5 #pw+1234567890+1# Provider Lock Status. (use the "*"
button
to obtain the "p,w" and "+" symbols)
6 #pw+1234567890+2# Network Lock Status. (use the "*" button
to
obtain the "p,w" and "+" symbols)
7 #pw+1234567890+3# Country Lock Status. (use the "*" button
to
obtain the "p,w" and "+" symbols)
8 #pw+1234567890+4# SIM Card Lock Status.(use the "*" button
to
obtain the "p,w" and "+" symbols)
9 *#147# (vodafone) this lets you know who called you last
*#1471# Last call (Only vodofone)
10 *#21# Allows you to check the number that "All Calls" are
diverted To
11 *#2640# Displays security code in use
12 *#30# Lets you see the private number
13 *#43# Allows you to check the "Call Waiting" status of your
phone.
14 *#61# Allows you to check the number that "On No Reply"
calls
are diverted to
15 *#62# Allows you to check the number that "Divert If Unrea
chable(no service)" calls are diverted to
16 *#67# Allows you to check the number that "On Busy Calls"
are
diverted to
17 *#67705646#R emoves operator logo on 3310 & 3330
18 *#73# Reset phone timers and game scores
19 *#746025625# Displays the SIM Clock status, if your phone
supports this power saving feature "SIM Clock Stop Allowed", it
means you will get the best standby
time
possible
20 *#7760# Manufactures code
21 *#7780# Restorefa ctory settings
22 *#8110# Software version for the nokia 8110
23 *#92702689# (to rember *#WAR0ANTY#)
Displays -
1.Serial Number,
2.Date Made
3.Purchase Date,
4.Date of last repair (0000 for no
repairs),
5.Transfer User Data.
To exit this mode -you need to
switch
your phone off then on again
24 *#94870345123456789# Deactivate the PWM-Mem
25 **21*number# Turn on "All Calls" diverting to the phone
number
entered
26 **61*number# Turn on "No Reply" diverting to the phone
number
entered
27 **67*number# Turn on "On Busy" diverting to the phone number
entered
28 12345 This is the default security code press and hold #
Thursday, April 2, 2009
Nokia MOSH Shutdown is Official Now

---->>>>
Nokia has finally announced that it will be replaced by the Ovi Store starting May 1.
According to the "farewell mail" sent by Nokia to MOSH users, the service has only 30 days of life left, after which users will be redirected to the Ovi Store if caught trying to access MOSH. This also means that your MOSH account will no longer be accessible, and stuff that you have uploaded goes as well. The Ovi Store will require you to sign up again, which you can do here as of now.
MOSH had become a headache of sorts for Nokia thanks to some of the unmoderated content, which resulted in legal problems and copyright issues. The Ovi Store, on the other hand, will be a fully moderated, Nokia controlled environment, like the Apple App Store and the likes.
As for what to expect in the Ovi Store, the farewell mail gives some idea of that as well. The Store content will be heavily customizable and will be tailored to your needs based on your location and social preferences. There is a Social Discovery feature available as well with the Ovi Store, which will automatically allow content from your social networks to be prioritized and made available for download and repeat consumption. In short, localization and tailored content seems to be the Ovi Stores mantra.
If you're a heavy MOSH user, you might as well have a last look at the store because there isn't much time left now!
Google Search Exposes Credit Card Details

---->>>>
Just days after the Symantec credit card information leak fiasco was exposed by BBC News, there is more bad news for credit card users in the UK.
This is because personal and credit card details of thousands of Visa, Mastercard, and American Express customers were listed online and were freely accessible via a simple Google search. About 19,000 Brits are allegedly affected.
According to media reports, the information was first posted on an unsecured server in Vietnam, used by fraudsters. The site was closed down in February, but the information remained available on Google.
Telegraph.co.uk quoted UK trade association for payments APACS spokesperson as saying that most of the cards on the list had already been cancelled, but there are concerns that their owners were not made aware of the fact that their credit card details had been leaked online. The report added that a Google spokesman said that the information has now been removed.
Rapidshare Tricks Part (1) : Bypass 1 Hour Download Limit

---->>>>
Option 1 : (For Dynamic IP Users)
The easy and best solution is, disconnect or restart your modem. This may change your IP address and you can continue to download the next file in rapidshare.
Option 2 :
Many peoples have lots of problem in downloading from Rapidshare. this post is specially for my broadband user friends.
1. Click Start
2. Click run
3. In the run box type "cmd" (without quotes) and click OK
4. When the command prompt opens type the following and hit enter after every new line.
ipconfig /flushdns
ipconfig /release
ipconfig /renew
exit
Explanation :
As all Broadband users has dynamic ip they can simply change their ip address. by the commands mentioned above.
If you are bore of typing this much Command then simply make a batch file.
Creating a Batch file.
* Open a notepad. type following in it.
@echo off
ipconfig /flushdns
ipconfig /release
ipconfig /renew
@echo on
* Save this file with name you like and the extension as bat.
* now simply execute this file.
Enjoy the Download.
Wednesday, February 18, 2009
Charge Dropped Against Pirate Bay Four
---->>>>
A Swedish prosecutor on Tuesday dropped a charge levied against four men on trial for running The Pirate Bay, one of the most popular BitTorrent search engines and trackers on the Internet.
Tuesday's proceedings saw Swedish prosecutor Håkan Roswall drop a charge of aiding in the making of copies of works under copyright, said Peter Sunde, one of the four on trial. The charge was dropped due to the inability of the prosecution to prove copies of content were made, he said.
"We have definitely won this round," Sunde said.
One charge -- essentially aiding the making of material under copyright available -- remains. Sunde and the other three defendants, Fredrik Neij, Gottfrid Svartholm Warg and Carl Lundström, could face prison time. Swedish authorities want them to forfeit 1.2 million Swedish kronor (US$140,000) in advertising revenue generated from the site.
A lawyer for the music industry, Peter Danowsky, denied that dropping the charge hurt the overall case.
"It's a largely technical issue that changes nothing in terms of our compensation claims and has no bearing whatsoever on the main case against The Pirate Bay," Danowsky said in a statement published by The Local, a Swedish newspaper published in English. "In fact it simplifies the prosecutor's case by allowing him to focus on the main issue, which is the making available of copyrighted works," he said in a statement.
The Motion Picture Association is seeking 93 million Swedish kronor in damages, and the IFPI (International Federation of the Phonographic Industry) is seeking €1.6 million (US$2.06 million) in damages.
Evidence presented by Roswall on Tuesday included screenshots showing computers were connected to The Pirate Bay's tracker, or software that coordinates P-to-P (peer-to-peer) file sharing.
But a majority of the screenshots show that The Pirate Bay was actually down at the time and that the client connections timed out, Sunde said. The clients, or peers, were still connecting with each other, but through a distributed hash table, another protocol for coordinating downloads unrelated to The Pirate Bay.
The schedule for Wednesday includes testimony from a Swedish antipiracy agency as well as the Motion Picture Association, Sunde said.
Also visit "The Pirate Bay News Trail"
A Swedish prosecutor on Tuesday dropped a charge levied against four men on trial for running The Pirate Bay, one of the most popular BitTorrent search engines and trackers on the Internet.
Tuesday's proceedings saw Swedish prosecutor Håkan Roswall drop a charge of aiding in the making of copies of works under copyright, said Peter Sunde, one of the four on trial. The charge was dropped due to the inability of the prosecution to prove copies of content were made, he said.
"We have definitely won this round," Sunde said.
One charge -- essentially aiding the making of material under copyright available -- remains. Sunde and the other three defendants, Fredrik Neij, Gottfrid Svartholm Warg and Carl Lundström, could face prison time. Swedish authorities want them to forfeit 1.2 million Swedish kronor (US$140,000) in advertising revenue generated from the site.
A lawyer for the music industry, Peter Danowsky, denied that dropping the charge hurt the overall case.
"It's a largely technical issue that changes nothing in terms of our compensation claims and has no bearing whatsoever on the main case against The Pirate Bay," Danowsky said in a statement published by The Local, a Swedish newspaper published in English. "In fact it simplifies the prosecutor's case by allowing him to focus on the main issue, which is the making available of copyrighted works," he said in a statement.
The Motion Picture Association is seeking 93 million Swedish kronor in damages, and the IFPI (International Federation of the Phonographic Industry) is seeking €1.6 million (US$2.06 million) in damages.
Evidence presented by Roswall on Tuesday included screenshots showing computers were connected to The Pirate Bay's tracker, or software that coordinates P-to-P (peer-to-peer) file sharing.
But a majority of the screenshots show that The Pirate Bay was actually down at the time and that the client connections timed out, Sunde said. The clients, or peers, were still connecting with each other, but through a distributed hash table, another protocol for coordinating downloads unrelated to The Pirate Bay.
The schedule for Wednesday includes testimony from a Swedish antipiracy agency as well as the Motion Picture Association, Sunde said.
Also visit "The Pirate Bay News Trail"
BitDefender Partner Site Hit by Hackers
---->>>>

Hackers elicited customer details from a Portuguese partner site associated with the security company BitDefender, the second intrusion in recent days targeting computer security companies.
The details are posted on hackersblog.org, which publishes information on security problems but says it will notify Web site operators and not reveal sensitive data.
The hackers used a form of a SQL injection attack to reveal personal details and e-mail addresses. SQL injection, one of the most common types of attacks, involves inputting commands into Web-based forms or URLs (Uniform Resource Locators) in order to return data held in back-end databases.
A 2006 survey by the Web Application Security Consortium of 31,373 sites found more than 25 percent were vulnerable to SQL injection, with more than 85 percent vulnerable to cross-site scripting attacks.
Screenshots posted on the blog show how the hackers were able to see data they shouldn't, although they took care to black out sensitive data.
BitDefender said the site was shut down after the vulnerability was found, and reopened on Monday around 6 p.m. GMT. BitDefender believes that none of the data exposed will be used for malicious purposes and that the attack was intended to illustrate the vulnerability. No customer credit card data was stored on the site, the company said.
BitDefender said it advises partners on good security practices but that "we can't control how our partners manage their sites."
Major computer security companies have seen their sites come under attack, highlighting how even organizations with deep knowledge of the dangers of hacking can still be caught off guard.
Last weekend, a hacker broke into part of Russian security company Kaspersky Lab's new U.S. support Web site. Company officials confirmed a programming flaw left the site open to SQL injection. The hacker could have accessed about 2,500 customer e-mail addresses and perhaps 25,000 product activation codes.
In July 2008, a Malaysian partner site for Kaspersky was defaced as it was still under development, although no sensitive data was lost.

Hackers elicited customer details from a Portuguese partner site associated with the security company BitDefender, the second intrusion in recent days targeting computer security companies.
The details are posted on hackersblog.org, which publishes information on security problems but says it will notify Web site operators and not reveal sensitive data.
The hackers used a form of a SQL injection attack to reveal personal details and e-mail addresses. SQL injection, one of the most common types of attacks, involves inputting commands into Web-based forms or URLs (Uniform Resource Locators) in order to return data held in back-end databases.
A 2006 survey by the Web Application Security Consortium of 31,373 sites found more than 25 percent were vulnerable to SQL injection, with more than 85 percent vulnerable to cross-site scripting attacks.
Screenshots posted on the blog show how the hackers were able to see data they shouldn't, although they took care to black out sensitive data.
BitDefender said the site was shut down after the vulnerability was found, and reopened on Monday around 6 p.m. GMT. BitDefender believes that none of the data exposed will be used for malicious purposes and that the attack was intended to illustrate the vulnerability. No customer credit card data was stored on the site, the company said.
BitDefender said it advises partners on good security practices but that "we can't control how our partners manage their sites."
Major computer security companies have seen their sites come under attack, highlighting how even organizations with deep knowledge of the dangers of hacking can still be caught off guard.
Last weekend, a hacker broke into part of Russian security company Kaspersky Lab's new U.S. support Web site. Company officials confirmed a programming flaw left the site open to SQL injection. The hacker could have accessed about 2,500 customer e-mail addresses and perhaps 25,000 product activation codes.
In July 2008, a Malaysian partner site for Kaspersky was defaced as it was still under development, although no sensitive data was lost.
Conficker Worm Draws a Counter-Attack
---->>>>
In response to the Conficker worm's massive infection of millions of PCs worldwide, industry heavyweights including Microsoft, Symantec and others today announced they're forming a new team to fight back against the worm.
In addition to the team's mission to grab domain names Conficker (aka Downadup) might try to use, Microsoft is offering a fat $250,000 reward for information that leads to the arrest and conviction of those responsible for the worm. The reward is available to residents of any country, Microsoft says.
Conficker's Achilles heel is its need to receive orders from a server on the Internet. The worm checks a list of up to 250 different domain names each day for instructions.
Normally, cycling through 250 different names would likely be enough to ensure that the good guys would be unable to keep up, as Conficker's controllers would theoretically only have to register one of those domains per day to control their massive herd of malware. But Conficker's notoriety has prompted the companies to coordinate their efforts and try to nab all the potential domain registrations before the bad guys can.
Doing so would restrict the worm to receiving updates or instructions only through its secondary peer-to-peer capability, according to Symantec. From the description, that secondary ability would likely limit the worm to making a peer-to-peer connection only with infected PCs on the same local network.
According to Symantec's announcement, the team includes "Microsoft, ICANN, Neustar, Verisign, CNNIC, Afilias, Public Internet Registry, Global Domains International Inc., M1D Global, AOL, F-Secure, ISC, researchers from Georgia Tech, The Shadowserver Foundation, Arbor Networks, and Support Intelligence."
If anyone does manage to register one of the domains before the team does, the team will investigate its owner.
This is a good step, and one I'd sure like to see taken further. This team should stick around after Conficker and continue to work to deny the bad guy's use of domain names, hosting providers and other infrastructure required by the malware black market.
I do wonder, though, why Microsoft didn't set up a phone number or other central point of contact for collecting information about Conficker. The company says that "individuals with information about the Conficker worm should contact their international law enforcement agencies."
In response to the Conficker worm's massive infection of millions of PCs worldwide, industry heavyweights including Microsoft, Symantec and others today announced they're forming a new team to fight back against the worm.
In addition to the team's mission to grab domain names Conficker (aka Downadup) might try to use, Microsoft is offering a fat $250,000 reward for information that leads to the arrest and conviction of those responsible for the worm. The reward is available to residents of any country, Microsoft says.
Conficker's Achilles heel is its need to receive orders from a server on the Internet. The worm checks a list of up to 250 different domain names each day for instructions.
Normally, cycling through 250 different names would likely be enough to ensure that the good guys would be unable to keep up, as Conficker's controllers would theoretically only have to register one of those domains per day to control their massive herd of malware. But Conficker's notoriety has prompted the companies to coordinate their efforts and try to nab all the potential domain registrations before the bad guys can.
Doing so would restrict the worm to receiving updates or instructions only through its secondary peer-to-peer capability, according to Symantec. From the description, that secondary ability would likely limit the worm to making a peer-to-peer connection only with infected PCs on the same local network.
According to Symantec's announcement, the team includes "Microsoft, ICANN, Neustar, Verisign, CNNIC, Afilias, Public Internet Registry, Global Domains International Inc., M1D Global, AOL, F-Secure, ISC, researchers from Georgia Tech, The Shadowserver Foundation, Arbor Networks, and Support Intelligence."
If anyone does manage to register one of the domains before the team does, the team will investigate its owner.
This is a good step, and one I'd sure like to see taken further. This team should stick around after Conficker and continue to work to deny the bad guy's use of domain names, hosting providers and other infrastructure required by the malware black market.
I do wonder, though, why Microsoft didn't set up a phone number or other central point of contact for collecting information about Conficker. The company says that "individuals with information about the Conficker worm should contact their international law enforcement agencies."
Hacker Gang Targets Security Companies
---->>>>
A hacker gang, purportedly from Romania, is using SQL injection attacks against security software companies.
Last week it was Kaspersky who was attacked, although the company denied that any real compromise had occurred. The hackers only actually exposed table names from the database, not actual data.
Later reports on that attack stated that the same gang was responsible for attacks on a Portuguese reseller for Bitdefender.
Now F-Secure is saying they were attacked, although once again they with only some success. They had a weak spot in their database-facing web pages that gather malware statistics. The page didn't properly "sanitize database inputs." SQL injection involves using database input fields to add SQL commands. Click here for a humorous and illustrative example.
F-Secure says the hackers, the same bunch responsible for the previous attacks, were able to read, but not manipulate the data. It sounds like they employ a good collection of security practices to employ defense-in-depth: hackers got through to the database, but other defenses stopped them there. The user account they compromised only had access to the malware measurement data, which is public anyway, and they couldn't write to the database.
A hacker gang, purportedly from Romania, is using SQL injection attacks against security software companies.
Last week it was Kaspersky who was attacked, although the company denied that any real compromise had occurred. The hackers only actually exposed table names from the database, not actual data.
Later reports on that attack stated that the same gang was responsible for attacks on a Portuguese reseller for Bitdefender.
Now F-Secure is saying they were attacked, although once again they with only some success. They had a weak spot in their database-facing web pages that gather malware statistics. The page didn't properly "sanitize database inputs." SQL injection involves using database input fields to add SQL commands. Click here for a humorous and illustrative example.
F-Secure says the hackers, the same bunch responsible for the previous attacks, were able to read, but not manipulate the data. It sounds like they employ a good collection of security practices to employ defense-in-depth: hackers got through to the database, but other defenses stopped them there. The user account they compromised only had access to the malware measurement data, which is public anyway, and they couldn't write to the database.
New Attacks Target IE7 Flaw
---->>>>
Internet attack trackers and antivirus companies warn that a flaw in Internet Explorer 7 (but not earlier versions) that Microsoft just patched last week is under attack in the wild. The attacks appear to be targeted and small-scale right now, but will likely grow.
Trend Micro describes a somewhat roundabout attack that starts with an e-mailed .doc file that, when opened, exploits the MS09-002 vulnerability to download and install remote-control backdoor malware.
Trend writes that this approach is likely part of a targeted attack. Such assaults typically involve more legwork on the part of crooks to construct a realistic spam message that may appear to come from a co-worker, for instance, and have a poisoned .doc or other file attached.
But the Internet Storm Center warns that while antivirus vendors currently only report .doc-using attacks, "there is absolutely nothing preventing attackers from using the exploit in a drive-by attack." And they expect that to happen very soon.
The good news is that to protect yourself, you only need to make sure you've closed the hole by applying last week's patch. It was distributed via Automatic Updates, so you can double-check that you got it by running Windows Update. Or head to the Microsoft security bulletin.
Internet attack trackers and antivirus companies warn that a flaw in Internet Explorer 7 (but not earlier versions) that Microsoft just patched last week is under attack in the wild. The attacks appear to be targeted and small-scale right now, but will likely grow.
Trend Micro describes a somewhat roundabout attack that starts with an e-mailed .doc file that, when opened, exploits the MS09-002 vulnerability to download and install remote-control backdoor malware.
Trend writes that this approach is likely part of a targeted attack. Such assaults typically involve more legwork on the part of crooks to construct a realistic spam message that may appear to come from a co-worker, for instance, and have a poisoned .doc or other file attached.
But the Internet Storm Center warns that while antivirus vendors currently only report .doc-using attacks, "there is absolutely nothing preventing attackers from using the exploit in a drive-by attack." And they expect that to happen very soon.
The good news is that to protect yourself, you only need to make sure you've closed the hole by applying last week's patch. It was distributed via Automatic Updates, so you can double-check that you got it by running Windows Update. Or head to the Microsoft security bulletin.
Monday, February 16, 2009
The Pirate Bay: BitTorrent Tracker Goes on Trial
---->>>>

Swedish website, The Pirate Bay, which claims to be the world's largest illegal BitTorrent tracker will go under trail today.
The Pirate Bay does not host copyrighted content, but acts as a search engine for 'torrents' available online and directs users to pirated movies, music and other protected material.
Three of the website's co-founders - Fredik Neij, Gottfrid Svartholm Warg and Peter Sunde Kolmisoppi and Swedish dotcom millionaire Carl Lundstr m - are accused of helping millions of Internet users illegally download protected movies, music, and computer games. If convicted, they face up to two years in prison and a fine of up to 1.2 million kronor ($1,43,529).
Plaintiffs which includes Warner Bros, MGM Pictures, Colombia Pictures, 20th Century Fox, Sony BMG, Universal and EMI, argue that The Pirate Bay promotes copyright infringement, and has made millions in profits since its launch in 2003. They are claiming more than $100m in damages.
This present case was filled in May 2006, when police raided 10 different locations in central Sweden, seized servers and computer equipment and temporarily causing the site to go offline for three days.

Swedish website, The Pirate Bay, which claims to be the world's largest illegal BitTorrent tracker will go under trail today.
The Pirate Bay does not host copyrighted content, but acts as a search engine for 'torrents' available online and directs users to pirated movies, music and other protected material.
Three of the website's co-founders - Fredik Neij, Gottfrid Svartholm Warg and Peter Sunde Kolmisoppi and Swedish dotcom millionaire Carl Lundstr m - are accused of helping millions of Internet users illegally download protected movies, music, and computer games. If convicted, they face up to two years in prison and a fine of up to 1.2 million kronor ($1,43,529).
Plaintiffs which includes Warner Bros, MGM Pictures, Colombia Pictures, 20th Century Fox, Sony BMG, Universal and EMI, argue that The Pirate Bay promotes copyright infringement, and has made millions in profits since its launch in 2003. They are claiming more than $100m in damages.
This present case was filled in May 2006, when police raided 10 different locations in central Sweden, seized servers and computer equipment and temporarily causing the site to go offline for three days.
Saturday, February 14, 2009
Estimate any Website Value with Stimator
---->>>>
Stimator a good tool to calculate the website value in USD. If you are going to sell a website or a blog you can check your website value with Stimator.

Stimator calculates the value of website by
* Value
* Web Recoginition
* Popularity
* Web Volume
* Linking Data
* Inlinking Scores
* Social Score
Website : www.stimator.com
Stimator a good tool to calculate the website value in USD. If you are going to sell a website or a blog you can check your website value with Stimator.

Stimator calculates the value of website by
* Value
* Web Recoginition
* Popularity
* Web Volume
* Linking Data
* Inlinking Scores
* Social Score
Website : www.stimator.com
Find Out Rating for Your Website
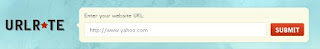
URL Rate is a free service which provides rate of the given URL.
---->>>>
URL Rate allows you to find out over all value for any website, just enter the website name and click submit. URL rate displays the information of the website like
* Domain Age
* Pagerank Check
* Inbound Links
* Traffic Rank
* Site Value Report
* URL Rating
*

Website : www.urlrate.com.
Microsoft to Pay $250,000 to Conficker Hunter

Microsoft will reward $250,000 to one who finds the culprit coder behind the Downadup/Conficker Work
---->>>>
Last month, a virus named Downadup/Conficker infected 9 million Windows machines and their network. Honestly, the virus created havoc by rapidly spreading within span of couple of days.
Post that, Microsoft has taken an active step by teaming up with Internet Corporation of Assigned Names and Numbers (ICANN), Domain Name System operators and others. Together they'll disable the domains targeted by conficker virus to stop the worm infection across the network.
George Stathakopulos, of Microsoft's Trustworthy Computing Group told BBC, "People who write this malware have to be held accountable." By collaborating with the technology companies, academic organizations and Internet Infrastructure firms, Microsoft intends to nail down the Conficker virus' activities.
Conficker virus is a self-replicating malware code that replicates itself over the computers and network without latest security patches. Security firms advices everyone to keep the virus definitions up to date and install Micrsoft MS08-67 patch (KB958644).
Microsoft has announced to pay reward of $250,000 to any individual who'll find out the culprits behind Conficker. Any individual of any country is eligible for this reward. Microsoft had paid $250,000 to two individuals who helped in identification of the notorious Sasser worm creators.
However, the crude reality also follows that rewards of $250,000 were also announced for other computer worms such as Blaster, MyDoom and Sobig but their culprits were never caught.
Microsoft to Open Retail Stores

To learn about consumer purchasing behavior
---->>>>
Microsoft has decided to step into retailing and will open Microsoft retail outlets. As per Microsoft's spokesperson, the company plans a 'small number' of stores. Microsoft obviously will be ridiculed for following a rival company's, Apple's, retail strategy. Microsoft intends to step into retailing to create a deeper engagement with consumers and to learn about their purchasing behavior.
David Porter, ex-Wal-Mart retail veteran, will join Microsoft as the corporate vice president of retail stores from 16th February. Porter, in the company's statement, said, "There are tremendous opportunities ahead for Microsoft to create a world-class shopping experience for its customers." Hence, it's clear that Microsoft wants to put Porter's retail experience to best use for their next retail venture.
Whether Microsoft likes it or not, a comparison with rival's, Apple's, retail store strategy is bound to happen. Apple's retail stores have highly trained sales staff, eye-catching store architecture, and their entire product line-up. Hence, the Microsoft retail store can also be expected to have trained sales staff and a variety of Microsoft-branded products.
What about the existing retail partners of Microsoft? Well, Microsoft intends to learn the first lessons in retailing themselves and then pass on the knowledge to their retail buddies, who are sure to be irked initially.
Microsoft will surely face challenges with the economic downturn on one hand and rival Apple's stable sales in the previous quarters on the other. Not surprisingly, Apple is also planning a major store space reorganization to emphasize more on consumer education, and software will be the primary focus.
Sunday, February 8, 2009
World Youngest iPhone Developer
---->>>>
A nine year old Malaysian boy Lim Ding Wen in Singapore has written painting application for Apple iPhone and he is also considered as the world youngest iPhone developer.
Lim Ding Wen wrote Doodle kids an iPhone application for his two younger sisters aged three and five.
World Youngest iPhone Developer

(Doodle Kids and Lim Ding Wen)
Doodle kids program has been downloaded more than 4,000 times from Apple’s iTunes store in less than two weeks.
His father Lim Thye Chean says, when Lim Ding Wen was 2 years old he learned how to insert a disk and boot a computer. At the age of seven Lim Thye Chean started teaching programming languages after he had done well in school.
Lim Ding Wen is fluent in six languages and completed 20 programming projects. His latest application Doodle Kids, allows users to draw pictures using their fingers and then clear the screen by shaking the iPhone.
A nine year old Malaysian boy Lim Ding Wen in Singapore has written painting application for Apple iPhone and he is also considered as the world youngest iPhone developer.
Lim Ding Wen wrote Doodle kids an iPhone application for his two younger sisters aged three and five.
World Youngest iPhone Developer

(Doodle Kids and Lim Ding Wen)
Doodle kids program has been downloaded more than 4,000 times from Apple’s iTunes store in less than two weeks.
His father Lim Thye Chean says, when Lim Ding Wen was 2 years old he learned how to insert a disk and boot a computer. At the age of seven Lim Thye Chean started teaching programming languages after he had done well in school.
Lim Ding Wen is fluent in six languages and completed 20 programming projects. His latest application Doodle Kids, allows users to draw pictures using their fingers and then clear the screen by shaking the iPhone.
Find Out who is Invisible in your Yahoo Messenger
---->>>>If you are using Yahoo Messenger now you can find out who is invisible, offline and online using 4invisible.
4Invisible is a website provides the status of an Yahoo id.
4 Invisible

Features
Easily used to find who is online, invisible and offline for any Yahoo id.
Website : www.4invisible.com
4Invisible is a website provides the status of an Yahoo id.
4 Invisible

Features
Easily used to find who is online, invisible and offline for any Yahoo id.
Website : www.4invisible.com
Thursday, February 5, 2009
Messack(Mobile Virus)

---->>>>
"Messack.sis" a small virus spreading very fastly in Indian cell phones. The source is Mp3 songs from different sites. Till date there is not any AntiVirus to destroy this virus. Before downloading or transferring any Mp3 song to your cell scan it with a good AntiVirus Software.
Wednesday, February 4, 2009
Google, NASA Launch Univ of Future

Preparing for an age when computers will be cleverer than humans
---->>>>
Google and NASA are already preparing themselves for the day when computers will be smarter than humans, according to a news report. The tech honchos have come together for a new university that will prepare scientists for an age when computers will be cleverer than humans.
Singularity University, as it will be known, will be based in NASA's Silicon Valley campus and will host its first class of 30 graduates this summer. This university aims to prepare future scientists for the time when machines use artificial intelligence to become sharper than human beings. It will help them to develop machines that would aid humans instead of harming them.
Google has already donated more than $1 million, and numerous other major companies are planning contribute at least $2,50,000.
We all know that we rush for to machines even when we are in the smallest dilemma. Machines have become our saviors in this modern age where we can trust a computer more than what we trust our fellow human beings. However, the day when these machines completely replace humans and become cleverer than us is not far away.
Google Internet Bus Comes to India

Life made simple with Internet
---->>>>
Google now aims to educate Indians about power of Internet with its 'Internet Bus'.
The Internet-enabled bus will focus on the four themes - education, information, communication, and entertainment. It will be loaded with useful and informative content in English and Tamil. Google said it will showcase how the Internet can make everyday life simple through services like search, email, social networking, maps and others.
The bus project took off from Chennai yesterday and will reach Vellore tomorrow and will cover numerous cities in Tamil Nadu over the next month and a half.
You can visit the Internet Bus Project website to see when the bus will visit your city; get regular updates. You can also check out photos and videos as Google travels around Tamil Nadu.
Here is the schedule that the Google Internet Bus will follow:
February
03 Feb Chennai
05 Feb Vellore
06 Feb Krishnagiri
07 Feb Salem
11 Feb Erode
12 Feb Tiruppur
14 Feb Coimbatore
18 Feb Dindigul
19 Feb Madurai
23 Feb Tirunelveli
25 Feb Nagercoil
27 Feb Tuticorin
March
02 Mar Pudukkottai
03 Mar Tiruchirappalli
06 Mar Thanjavur
08 Mar Kumbakonam
10 Mar Neyveli
12 Mar Cuddalore
13 Mar Tiruvannamalai
Yahoo Search Pad: Google Disposes, Yahoo Proposes

Makes online research easy
---->>>>
Only weeks after Google announced that it will stop its Notebook application for new users, Yahoo said it will launch something very similar to that under the name Search Pad.
Yahoo Search Pad detects users' research intent, automatically collecting visited sites, and providing tools for users to organize and add notes - all in one place. Users will be able to edit, delete, and re-order notes they've taken on a topic and then print them out or email them to friends and family through Search Pad. They can also save the notes to access later by logging in with their Yahoo! ID.
However, the Search Pad application is currently only in testing and is not visible to all users.
Tuesday, February 3, 2009
Microsoft Launches Windows 7 in Hindi

The new initiatives include Language Interface Packs (LIPs) in 12 Indian languages for MS Office and Windows
---->>>>
Microsoft, as a part of its efforts to overcome the language barrier to computing, has showcased a variety of custom made products directed specifically at the vernacular language market - a market that has been largely left untapped till now.
The new initiatives include Language Interface Packs (LIPs) in 12 Indian languages - Assamese, Bengali, Gujarati, Gurmukhi, Hindi, Kannada, Konkani, Malayalam, Marathi, Oriya, Tamil and Telugu - for MS Office and Windows.
The company has also announced a total of 45 additional virtual keyboards for these languages. Even Windows Live has not been spared the treatment with it being made available in as many as seven Indian languages. These languages are Gujarati, Hindi, Kannada, Malayalam, Marathi, Tamil and Telugu.
There's more in store for developers as well. Directed at vernacular language developers, it has launched the Captions Language Interface Pack (or CLIP) in Hindi, Malayalam, Oriya, and Tamil. CLIP uses a tool tip caption to display translations for user interface items in Visual Studio 2008 making it the first ever instance of Microsoft releasing a tool specifically to help students and beginner developers in India use the product in their own language.
The most talked about part of the sneak peek was a rather cool beta version of Windows 7 in Hindi, one of the eight global languages the Operating System (Beta) was released in recently. We would love to have a go at this one!
Beware! Airtel Warns Users of SMS Scam

Criminals devise new way to dupe innocent people
---->>>>
Cyber frauds are nothing new in India, every now and then we hear about people getting duped by unsolicited e-mails received from Nigeria, UK.
It seems criminals have devised a new way to dupe innocent people via SMS. An alert on Airtel's website is cautioning it's users to be vary of such fraudsters.
According to Airtel, "an instance has come to notice in one of the circles wherein some subscribers have received SMS of the type - !Urgent! Your number has been selected for a $5,000 prize guaranteed! To claim your prize call +423697497456/ +447024054367. The above SMS is sent through bulk SMS product and is a type of Premium Rate Service Fraud (PRS) operated by organized gangs. The intent of the SMS is to induce the subscribers to call international numbers as listed above which have very high terminating rates. When the subscriber calls the number he is usually connected to a recorded message and the customer is billed a high amount. Replying to such SMS's could also result in viruses being downloaded on the subscriber's phone."
The disclaimer put up on the Airtel website:
"Unsolicited fraudulent SMS's are being sent to various subscribers informing them that they have won a prize and need to call an international number to collect their prize. When calls are made to the number in the text message the subscribers are billed a high amount (upto Rs 500 per minute). Subscribers are cautioned not to respond to such SMS's."
But worry not, TRAI will now be able to nab mobile phone spammers.
Have you been victim to such fraud? Do let us know through your comments.
Nivio - India's Answer to Google's GDrive

Free online storage from NivoLite
---->>>>
While Google lovers anticipate the arrival of GDrive, some others are already offering storage in the online space. One of the newest online storage space providers is NivioLite Free, an online computing utility that offers free online storage and backup facility.
NivioLite Free is offering a measly 1GB storage capacity in the times when Microsoft already has its Skydrive in place which offers 25GB of online storage -- at no cost.
How much can 1GB of storage house? Around 200 songs or 400 photos, says NivioLite's developers. If you need anything more than 1GB, you will have to purchase the extra space for 3 pounds to access Nivio's full service. With the upgrade you will get full access to Nivio s virtual Windows Desktop where one can create and edit files. This also includes the nDrive - a user intuitive tool that facilitates an easy and quick transfer of files between a local computer and the Nivio online desktop.
It isn't difficult to acquire hundreds of music files over a little period of time, and 1GB would definitely not suffice. This new service seems to be for the ignoramus as only those who do not know about the existing high-capacity online storage facilities would want to bother to register for a 1GB storage service.
On another note, 10-year old Yahoo Briefcase service which offers users 25MB of storage will be shutting on March 30. Unless newbie NivioLite plans to offer a mass-appealing online storage capacity, it could remain the storage house for a niche segment of users.
Is Apple Readying Dual-core, Quad-core iMacs?

Currently, Apple offers iMacs in 20-inch and 24-inch sizes, with two different configurations for each size.
---->>>>
Long due iMac upgrades have slowly started tipping rumors. The rumor mills are now eyeing Apple's iMac for update since the Mac Mini didn't get any update in recent MacWorld expo. It's been rumoured that Apple is going to refresh the iMacs with dual-core and quad-core processors according to a report by CNET.
Shaw Wu, of Kaufman Brothers, believes that Apple will be updating the iMacs line up. Currently, Apple offers iMacs in 20-inch and 24-inch sizes, with two different configurations for each size.
The new refreshed iMacs will get a high-end quad-core chip and a low-cost dual-core processor. The highest-end 24-inch iMac will get a high-end quad-core processor while the 20-inch version will get a low-cost dual-core processor. These new iMacs can be expected soon as Apple has reportedly decided to reduce 24-inch iMacs shipments in coming weeks.
To complement this rumor, Intel is set to launch new quad-core server processors by end-March which might be used for new Mac Pro iterations.
If this stand's true, Apple fans will get to choose dual-core and quad-core iMacs. Recently, many OEMs like HP, Asus, Lenovo and LG have come out with all-in-one style computers. To lead this segment, Apple really should refresh its product line-up.
SMS Malware Targets Nokia S60 Mobiles

Curse of Silence worm enters your phone in the form of a simple text message and stops incoming SMSes
---->>>>
A new SMS worm that targets certain Series 60 third edition devices has been detected. Before you start panicking, don't worry, there is a fix.
The "Curse of Silence" worm comes to your inbox in the form of a simple text message and then goes ahead to ensure that you don't receive any further SMSes. The worm affects Series 60 third edition handsets and some UIQ based handsets running (S 60) versions 2.6, 2.8, 3.0, and 3.1. The worm was first detected towards the end of last year, and has been listed by F-Secure as a threat. While some may term it as a virus, the notable thing is that it makes use of a security hole in S60 to execute its attack.
The attack begins with the target phone receiving an "infected" SMS. The behavior of the worm after this differs from device to device. While some older devices stop receiving SMS/MMS right after the first SMS is received, some others require quite a few messages before going kaput. The device, once affected, displays a message saying that the message memory is full and that there is no space remaining for more messages. Till now, the only way for a phone to recover from such an attack was a factory reset.
Nokia has, however, released a fix called the SMS cleaner, which apparently fixes the hole. F-Secure has further details on the worm. Check it out here.
Yahoo to Shut Down Briefcase Service

---->>>>
The company has cited low usage and popularity of the service when compared to its other services like Flickr and Mail as reasons for pulling the plug
E-Mail Print
Yahoo, as a part of trimming down excess baggage, has decided to shut down its 10-year-old online storage program -- the Yahoo Briefcase.
The company has cited low usage and popularity of the service when compared to its other services like Flickr and Mail as reasons for pulling the plug.
Users have been provided a March 30 deadline to retrieve their data stored online. Yahoo adds that discontinuing the service will allow them to focus their efforts on more broadly used products.
This comes days after new Yahoo CEO Carol Bartz took charge and is on a mission to save the Internet giant with a series of tough measures that included even more lay-offs, pay cuts and salary freezes.
Those of you who still use the service might as well save all your files back to your PCs before the March 30 deadline - lest you lose your data permanently.
Man Killed in Mobile Phone Explosion

Incident might have occurred due to one of those cheap duplicate batteries
---->>>>
Here's one more reason to stay away from those spurious batteries.
A 20 year-old Chinese youngster died when a battery inside the phone he was carrying in his pocket exploded, severing his arteries leading to massive blood loss and eventual death. According to some reports, the person had recently changed his phone battery and had charged the same moments before the fatal accident. The accident occurred in front of a Lenovo store in Guangzhou, China.
Exploding phone batteries are not a new phenomenon. However, fatalities from such occurrences are rare and this one just might be the worst ever recorded. The incident also makes us wonder if it is really worth saving money when it comes to batteries. While we still do not have details regarding the phone or the kind of battery that was involved in the incident, it is likely that this might be one of those cheap duplicate batteries.
We hope your plans to invest in a "cheaper" option might have been thwarted by this unfortunate incident.
3D View of Mars, Ocean with Google Earth 5

---->>>>
Do you want to dive into the ocean and explore the nooks and crannies of the seafloor? Want to step on Mars and experience how it feels to be on the red planet? Now you will be able to experience all this and more from your PC, thanks to the newest version of Google Earth.
With Google Earth 5.0, you can explore thousands of data points including videos and images of ocean life, details on the best surf spots, logs of real ocean expeditions, and much more. With this new feature, you can now move back and forth in time while exploring a place to reveal imagery from years and even decades past, revealing changes over time.
This new-fangled Google Earth also has a Touring feature which makes it simple to create sharable, narrated, fly-through tour by clicking the record button and navigating through your tour destinations. By selecting "Mars" from the toolbar in Google Earth, one can access a 3D map of the planet featuring the latest high-resolution imagery, 3D terrain, and annotations showing landing sites.
Download Google Earth 5.0
Saturday, January 31, 2009
Global Recession Increases Risk of IP
---->>>>

Data losses by companies worldwide amounted to $1 trillion, which had $4.6 billion worth of intellectual property loss, said a report released by McAfee.
In the global meltdown, companies face pressures to reduce spending and cut staffs, which can create porous defenses and increased opportunity for crime. Companies need to stop looking at security as a cost center, but as a business enabler, said the report.
"Companies are grossly underestimating the loss and value of their intellectual property," said Eugene Spafford, professor of computer science at Purdue University and executive director of Center for Education and Research in Information Assurance and Security (CERIAS).
Key findings of the report are:
Recession puts intellectual property at risk
- 39% of respondents surveyed believe vital information is more vulnerable in the current economic climate than before.
Commitment to protecting vital information varies
- 74% of Chinese and 68% of Indian respondents invested in securing their intellectual property for competitive advantage
Intellectual property is now an international currency
- An emerging target for cybercriminals is intellectual property, and experts say there has been an increase in the number of corporate data intrusions by organized cyber mafia gangs
Employees steal intellectual property for financial gain and competitive advantage
- An increasing number of financially-challenged employees are using their corporate data access to steal vital information.
- 42 % of respondents said displaced employees were the biggest threat to vital information.
Geographic threats to intellectual property
- Geopolitical perceptions are influencing data policy reality. China, Pakistan and Russia were identified by companies surveyed as trouble zones for various legal, cultural and economic reasons

Data losses by companies worldwide amounted to $1 trillion, which had $4.6 billion worth of intellectual property loss, said a report released by McAfee.
In the global meltdown, companies face pressures to reduce spending and cut staffs, which can create porous defenses and increased opportunity for crime. Companies need to stop looking at security as a cost center, but as a business enabler, said the report.
"Companies are grossly underestimating the loss and value of their intellectual property," said Eugene Spafford, professor of computer science at Purdue University and executive director of Center for Education and Research in Information Assurance and Security (CERIAS).
Key findings of the report are:
Recession puts intellectual property at risk
- 39% of respondents surveyed believe vital information is more vulnerable in the current economic climate than before.
Commitment to protecting vital information varies
- 74% of Chinese and 68% of Indian respondents invested in securing their intellectual property for competitive advantage
Intellectual property is now an international currency
- An emerging target for cybercriminals is intellectual property, and experts say there has been an increase in the number of corporate data intrusions by organized cyber mafia gangs
Employees steal intellectual property for financial gain and competitive advantage
- An increasing number of financially-challenged employees are using their corporate data access to steal vital information.
- 42 % of respondents said displaced employees were the biggest threat to vital information.
Geographic threats to intellectual property
- Geopolitical perceptions are influencing data policy reality. China, Pakistan and Russia were identified by companies surveyed as trouble zones for various legal, cultural and economic reasons
Over 90% Emails Are Spam & Malware
---->>>>

Getting spam email in your inbox is everyone's daily headache. What we did not realize till now is the magnitude of the problem. Panda Security analyzed over 430 million email messages in 2008 and the results were scary.
Out of all the email messages analyzed, 89.88% turned out to be spam and 1.11% were infected with some type of malware. In the last three months of the year, 301,000 zombie computers were activated and used for distributing spam
"For companies, spam is more than just a nuisance: It consumes bandwidth, wastes employees' time and can even cause system malfunctions. In the end, it all results in a loss of productivity," Luis Corrons, technical director of PandaLabs.
Much of this spam was circulated by the extensive network of zombie computers controlled by cyber-crooks. A zombie is a computer infected by a bot, a type of malware allowing cyber criminals to control infected systems. Frequently, these computers are used as a network to drive malicious actions such as the sending of spam. Just in the last three months of the year, 301,000 zombie computers were being put into action every day.

Sexual enhancements, pharmacy are among favorite subjects
With respect to the different types of spam in circulation, 32.25% of spam in 2008 was related to pharmaceutical products with sexual performance enhancers accounting for 20.5%.
Spam relating to the economic situation also grew significantly throughout 2008. False job offers and fraudulent diplomas accounted for 2.75% of all junk mail in the year, while messages promoting mortgages and fake loans were responsible for 4.75%.
Spam promoting fake brand products was responsible for 16.75% of the total. This last category nevertheless, dropped from 21% in the first half of the year to 12.5% in the last six months.

Getting spam email in your inbox is everyone's daily headache. What we did not realize till now is the magnitude of the problem. Panda Security analyzed over 430 million email messages in 2008 and the results were scary.
Out of all the email messages analyzed, 89.88% turned out to be spam and 1.11% were infected with some type of malware. In the last three months of the year, 301,000 zombie computers were activated and used for distributing spam
"For companies, spam is more than just a nuisance: It consumes bandwidth, wastes employees' time and can even cause system malfunctions. In the end, it all results in a loss of productivity," Luis Corrons, technical director of PandaLabs.
Much of this spam was circulated by the extensive network of zombie computers controlled by cyber-crooks. A zombie is a computer infected by a bot, a type of malware allowing cyber criminals to control infected systems. Frequently, these computers are used as a network to drive malicious actions such as the sending of spam. Just in the last three months of the year, 301,000 zombie computers were being put into action every day.

Sexual enhancements, pharmacy are among favorite subjects
With respect to the different types of spam in circulation, 32.25% of spam in 2008 was related to pharmaceutical products with sexual performance enhancers accounting for 20.5%.
Spam relating to the economic situation also grew significantly throughout 2008. False job offers and fraudulent diplomas accounted for 2.75% of all junk mail in the year, while messages promoting mortgages and fake loans were responsible for 4.75%.
Spam promoting fake brand products was responsible for 16.75% of the total. This last category nevertheless, dropped from 21% in the first half of the year to 12.5% in the last six months.
Nano Computers for Rs. 500
---->>>>

The computer is developed by the Indian Institute of Technology, Chennai, and the Indian Institute of Science, Bangalore
E-Mail Print
Forget MIT's $100 laptop, "cheap" netbooks, and other crude attempts at making the computer affordable. Here comes the mother of all low-cost computers.
At Rs. 500, the upcoming, yet to be named, nano computer is set to be the cheapest computing device ever. Designed for students, the Government is supposedly readying a prototype of the device to be showcased at Tirupati on February 3, 2009. India's Human Resource Minister Arjun Singh will reportedly unveil the device.
The nano computer has been jointly developed by the IIT (Indian Institute of Technology), Chennai, and the IISc (Indian Institute of Science), Bangalore. The production of the device, however, has been handed over to private firms. It remains to be seen if this project manages to move past the "prototype" phase to actually end up in some assembly line.

The computer is developed by the Indian Institute of Technology, Chennai, and the Indian Institute of Science, Bangalore
E-Mail Print
Forget MIT's $100 laptop, "cheap" netbooks, and other crude attempts at making the computer affordable. Here comes the mother of all low-cost computers.
At Rs. 500, the upcoming, yet to be named, nano computer is set to be the cheapest computing device ever. Designed for students, the Government is supposedly readying a prototype of the device to be showcased at Tirupati on February 3, 2009. India's Human Resource Minister Arjun Singh will reportedly unveil the device.
The nano computer has been jointly developed by the IIT (Indian Institute of Technology), Chennai, and the IISc (Indian Institute of Science), Bangalore. The production of the device, however, has been handed over to private firms. It remains to be seen if this project manages to move past the "prototype" phase to actually end up in some assembly line.
Google's GDrive Could Replace your Hard Disk
---->>>>

This drive will allow users to save their data online and users will be able to access their data from any computer in the world
E-Mail Print
Taking cloud computing to a new level, Google is soon going to launch 'GDrive', a long-rumored online storage for its users.
GDrive would work as an online hard disk and could essentially work as a syncing device that will periodically update itself with the activities that take place on a computer, the Google Operating System has discovered.
Also discovered in a Google Apps CSS file is that there is reportedly an update for Google Docs on the way that would include a desktop client for syncing files with GDrive.
Since this drive will allow users to save their data online, users will be able to access their data from any computer in the world, as long as it is connected to an internet connection.
In fact, if you take Google provisions seriously, you've probably already shifted your photograph and document base to atleast one of the Google services that work as great archiving hubs. However, space restriction and reliability could be a user's concern while depending on the Google servers to save their precious data.
The GDrive could also partially replace the physical hard disk that a user needs to select an operating system (OS) for usage -- that is, after the initial booting. Google's online hard drive will merge all of Google's web based applications and make them available together.
The GDrive is expected to be launched in Later 2009.

This drive will allow users to save their data online and users will be able to access their data from any computer in the world
E-Mail Print
Taking cloud computing to a new level, Google is soon going to launch 'GDrive', a long-rumored online storage for its users.
GDrive would work as an online hard disk and could essentially work as a syncing device that will periodically update itself with the activities that take place on a computer, the Google Operating System has discovered.
Also discovered in a Google Apps CSS file is that there is reportedly an update for Google Docs on the way that would include a desktop client for syncing files with GDrive.
Since this drive will allow users to save their data online, users will be able to access their data from any computer in the world, as long as it is connected to an internet connection.
In fact, if you take Google provisions seriously, you've probably already shifted your photograph and document base to atleast one of the Google services that work as great archiving hubs. However, space restriction and reliability could be a user's concern while depending on the Google servers to save their precious data.
The GDrive could also partially replace the physical hard disk that a user needs to select an operating system (OS) for usage -- that is, after the initial booting. Google's online hard drive will merge all of Google's web based applications and make them available together.
The GDrive is expected to be launched in Later 2009.
Obama, McCain Cyber-attacks have Chinese Origins?
---->>>>

Government officials in the US suspect that a series of attacks on the US Presidential candidates Barack Obama and John McCain's campaign computer networks originated from China.
The attacks happened earlier this year when campaigning was in full swing; a large amount of information was successfully downloaded from the candidates' networks -- an attempt to learn in detail about the candidate's policies.
The officials at the moment are tight-lipped about the perpetrators who carried out these attacks. They have however stated that there is no confirmation if the acts were government-sponsored or an attention seeking attempt by a team of hackers.
The details were first revealed by Newsweek, which had then reported that the FBI and US Secret Service agents had informed the Obama team about the attacks and that there were doubts about possible Russian or Chinese hand behind the attacks. The Bush administration, since the breach, has ramped up cyber-security across all government organizations.
This comes barely an year after the Chinese military managed to hack in to the Pentagon systems -- the 2007 hack was thought to be the most serious security breach ever of the US Military's computer network.

Government officials in the US suspect that a series of attacks on the US Presidential candidates Barack Obama and John McCain's campaign computer networks originated from China.
The attacks happened earlier this year when campaigning was in full swing; a large amount of information was successfully downloaded from the candidates' networks -- an attempt to learn in detail about the candidate's policies.
The officials at the moment are tight-lipped about the perpetrators who carried out these attacks. They have however stated that there is no confirmation if the acts were government-sponsored or an attention seeking attempt by a team of hackers.
The details were first revealed by Newsweek, which had then reported that the FBI and US Secret Service agents had informed the Obama team about the attacks and that there were doubts about possible Russian or Chinese hand behind the attacks. The Bush administration, since the breach, has ramped up cyber-security across all government organizations.
This comes barely an year after the Chinese military managed to hack in to the Pentagon systems -- the 2007 hack was thought to be the most serious security breach ever of the US Military's computer network.
Check Internet Performance with Google's M-Lab
---->>>>

Have you been wondering whether you're getting the broadband connection you were promised by your Internet Service Provider (ISP)?
If your answer is yes, then you'd be happy to know that there are tools being devised by Google's M-Lab, 0r Measurement Lab, that can help get answers to your Internet's performance related questions.
Measuremt Lab Tools can help you test your broadband connection, including measuring its speed and evaluating the performance of certain applications.
M-Lab is at the beginning of its development and is only a "proof of concept", says the M-Lab disclaimer.
When announced, 3 tools will be available on 3 servers at one location, and the tools will only be able to support a limited number of simultaneous users. "We intend to greatly expand the variety of tools and the servers, as well as support more users. A total of 36 servers will be deployed across 12 locations early in 2009, and we hope to roll out others soon after," say the developers at M-Lab.
M-Lab will offer a Network Diagnostic Tool which helps test an Internet connection speed and also offers a diagnosis of problems limiting speed. Also offered is Glasnost, a tool meant to test whether your BitTorrent is being blocked. Lastly, Network Path and Application Diagnosis is a tool offered that diagnoses common problems that impact last-mile broadband networks.
Google will be hosting the tools on 37 servers in the U.S. and Europe.

Have you been wondering whether you're getting the broadband connection you were promised by your Internet Service Provider (ISP)?
If your answer is yes, then you'd be happy to know that there are tools being devised by Google's M-Lab, 0r Measurement Lab, that can help get answers to your Internet's performance related questions.
Measuremt Lab Tools can help you test your broadband connection, including measuring its speed and evaluating the performance of certain applications.
M-Lab is at the beginning of its development and is only a "proof of concept", says the M-Lab disclaimer.
When announced, 3 tools will be available on 3 servers at one location, and the tools will only be able to support a limited number of simultaneous users. "We intend to greatly expand the variety of tools and the servers, as well as support more users. A total of 36 servers will be deployed across 12 locations early in 2009, and we hope to roll out others soon after," say the developers at M-Lab.
M-Lab will offer a Network Diagnostic Tool which helps test an Internet connection speed and also offers a diagnosis of problems limiting speed. Also offered is Glasnost, a tool meant to test whether your BitTorrent is being blocked. Lastly, Network Path and Application Diagnosis is a tool offered that diagnoses common problems that impact last-mile broadband networks.
Google will be hosting the tools on 37 servers in the U.S. and Europe.
Saturday, January 24, 2009
Beware: iWork '09 from BitTorrent Has Trojan
---->>>>

Trojan infected pirated copy of iWork 09 for Mac OS X based systems has infected about 20,000 Mac computers worldwide
Intego, Mac-based security and anti-virus software makers, issued a security alert about a Trojan residing in the pirated Apple iWork 09 productivity suite. According to Intego's security alert, this pirated copy must've been downloaded about 20,000 times by now, and must've infected at least that many number of Mac systems.
Along with the pirated iWork 09 suite, an additional package, 'iWorkServices,' gets installed in the system. Once the installation process is complete, a Trojan horse - OSX.Trojan.iServices.A - gets installed as a start-up item and gets root level read-write permission. The Trojan horse then connects to remote servers over the web, but it doesn't carry the virus property of infecting other Mac systems.
The iWorkServices package in infected systems can be found in System/Library/Startup Items. The removal process suggested is re-installation of OS X since getting rid of infected components can be a tedious task.
The pirated copy is moving around on the web through BitTorrent sites. The iWork copies that are bought don't require a serial number, but a trial copy activation of iWork 09 will require a serial number.
Beware of the pirated copies, if you want to avoid infecting your systems.

Trojan infected pirated copy of iWork 09 for Mac OS X based systems has infected about 20,000 Mac computers worldwide
Intego, Mac-based security and anti-virus software makers, issued a security alert about a Trojan residing in the pirated Apple iWork 09 productivity suite. According to Intego's security alert, this pirated copy must've been downloaded about 20,000 times by now, and must've infected at least that many number of Mac systems.
Along with the pirated iWork 09 suite, an additional package, 'iWorkServices,' gets installed in the system. Once the installation process is complete, a Trojan horse - OSX.Trojan.iServices.A - gets installed as a start-up item and gets root level read-write permission. The Trojan horse then connects to remote servers over the web, but it doesn't carry the virus property of infecting other Mac systems.
The iWorkServices package in infected systems can be found in System/Library/Startup Items. The removal process suggested is re-installation of OS X since getting rid of infected components can be a tedious task.
The pirated copy is moving around on the web through BitTorrent sites. The iWork copies that are bought don't require a serial number, but a trial copy activation of iWork 09 will require a serial number.
Beware of the pirated copies, if you want to avoid infecting your systems.
Subscribe to:
Posts (Atom)
 RSS Feed (xml)
RSS Feed (xml)











